Q. FRAUD AWARENESS
How do you best protect against fraud the trust money that clients have entrusted to your firm? Educate yourself and others in your firm – lawyer and support staff alike – about the fraud risks and then creating and maintaining an environment of internal controls that helps prevent fraud.
Remember that this means protecting the channels by which you may receive trust money, or disburse it. For example:
- If your client is providing a cheque or bank draft, scrutinize it, does it look right?
- If you are acting on a collections matter and the opposing party provides the funds right away, does that make sense?
- If your client is pressuring you to disburse trust money in a hurry without following your firm’s established protocols, is that a warning sign?
- Are you being asked to change payout instructions late in the matter, inconsistent with the original instructions from your client?
- Do payment instructions make sense in the context of the matter? For example, if your client has recently moved to Alberta, why would they ask you to send funds out of Canada?
You should also know that beyond internal controls, you should always question the unusual when something doesn’t feel right. These questions should be investigated and resolved before accepting or disbursing trust money.
Be constantly diligent, as new fraud methods are relentlessly being developed and existing methods are being changed. Not all frauds will have the same red flags, but there are warning signs if you listen to them. Trust your instincts. Don’t forget basic security practices such as keeping passwords confidential, regularly changing passwords, and keeping your software up to date. Learn about social engineering scams that can often arrive by email and trick recipients into entering passwords or inadvertently allowing ransomware to be installed on your network.
In addition to having strong internal controls and adopting good cyber hygiene, you can SIGNIFICANTLY REDUCE the risk of all kinds threats to trust money by following the Safe Flow of Funds guideline every single time you handle trust money:
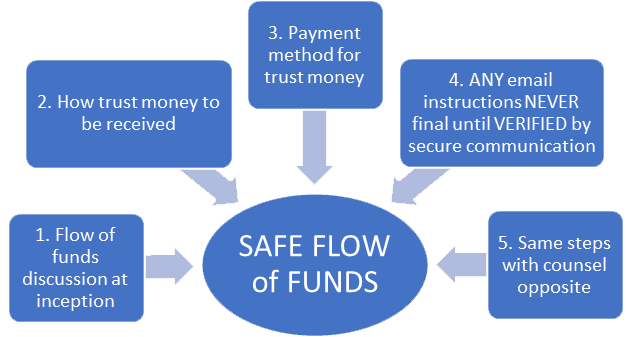
- Flow of funds discussion: Establish the flow of funds together with your client as early as possible. This is for funds to be received or disbursed.
- Receipt of trust money: Tell your client how you are to receive money in this matter, that your instructions will not change and to be automatically suspicious of such an event, calling you ONLY at the phone number they already have for you – NOT using any number accompanying the changed instruction!
- Payment of trust money: Obtain written payment instructions at that same meeting if you can, but that’s not always possible and remember there will be extra steps to verify any information received later.
- Payment instructions via email: If you EVER receive ANY payment instructions by email or fax– even initial instructions – have a two-part policy:
- they are NEVER considered to be final instructions until they are VERIFIED; and
- they can only be verified by using contact information other than those that accompany the instructions.
If this is your client providing payment instructions, confirm by PHONE on a call you initiate using the contact information you gathered at the start of the matter. If it’s another law firm, call the firm using the contact information from the Law Society’s website directory (Lawyer Lookup in Manitoba, with similar directories in other jurisdictions). Under NO circumstances should you confirm by email or call using contact information provided with the instructions.
- Counsel Opposite: Take the same precautions for money flowing from or to counsel opposite. Would-be thieves impersonate anybody involved in a transaction, including staff at another law firm.
Know that fraud risks exist both inside and outside of your firm. Proper controls, implemented consistently, and an appropriate level of oversight on an ongoing basis will help reduce these risks. Ensure new staff are trained properly. Check from time to time to make sure the controls are still working properly or are updated to reflect new practices.
For further information about good cyber hygiene, see the Cyber Security resource library.
